This article looks at how OAP over REST can be used to offer secure communication between OAM Servers and clients (OAM Agents) using the Access Protocol channel. In this case, we also provide advice on how to configure your WebGates.
What is an Oracle WebGate agent?
Any front-ending entity that serves as an access client to enable single sign-on across business applications is referred to as an agent (also known as a single sign-on agent or policy enforcement point, or PEP).
It functions as an Oracle Access Manager (OAM) web-server plug-in that catches HTTP requests and sends them to the Access Server for authentication and authorization. In order to establish the necessary trust mechanism between the agent and OAM Server, individual agents must be registered with Access Manager. The OAM Server receives authentication requests from registered agents.
The channel’s security level is stated in OAM 11g as either:
- Un-encrypted/ Open communication: The WebGate and OAM Server do not use encryption or authentication. The OAM Server accepts connections from all WebGates, and the WebGate does not request identification documentation from the OAM Server.
- Simple: Communication is encrypted using the Secure Sockets Layer (SSL) protocol and an Oracle public key certificate.
- Cert: SSL-encrypted communication with a public key certificate issued by a reliable third-party certificate authority (CA).
- OAP: If the user-defined parameter OAMServerCommunicationMode is set to OAP, WebGate connects with OAM controlled servers via legacy back channel Protocols, OAP over the TCP port, and communication mode Open, Simple, or Cert.
In OAM 12c, the channel’s security level can also be defined as one of the following:
- HTTP: User defined un-encrypted communication mode.If the user-defined parameter OAMServerCommunicationMode is set to HTTP, the webgate will use HTTP protocols to connect with the OAM controlled servers.
- HTTPS: User defined encrypted communication mode through the Secure Sockets Layer (SSL) protocol.
If the user-defined parameter OAMServerCommunicationMode is set to HTTPS, the webgate will use HTTPS protocols to connect with the OAM controlled servers.
OAM Servers and WebGates leverage these communication channels to authenticate and authorize users:
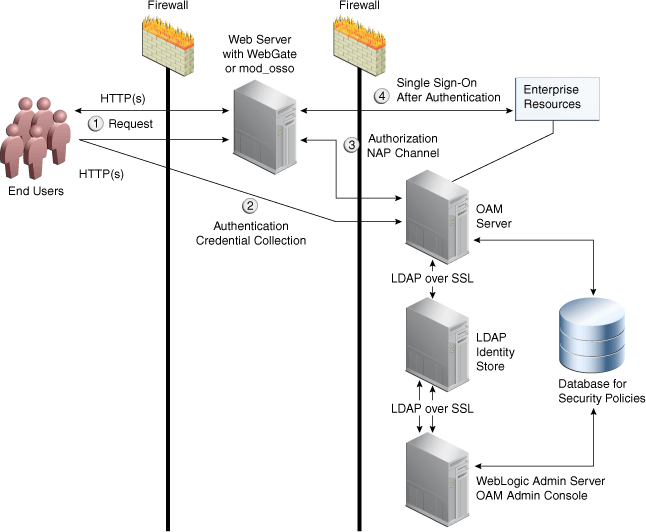
Figure : Communication Channels for OAM Servers and WebGates
- WebGate intercepts the request.
- Authentication (credential collection) occurs over HTTP(s) channel.
- Authorization occurs over the NAP (also known as the OAP) channel with OAM Agents only.
Securing Communication between OAM Servers and WebGates using OAP over REST:
The HTTP(S) transport technique between WebGate and the OAM server is enabled by OAP over REST. This transport method lowers operational costs for cloud and hybrid installations in which some components are on-premises and others are migrated to the cloud.
OAP adds an extra layer of security by encrypting messages transmitted to the server by default with RESTPayloadEncryption.
OAM server uses the following to facilitate HTTP(S) communication:
- REST endpoint: As server filter deployed on managedserver /iam/access/binding/api/v10/oap.
- Work Manager components
OAP over REST is the default mode of communication in this 12.2.1.4.0 release of Oracle Access Management. When you build an SSO agent, the following additional parameters are automatically set.
OAMRestEndPointHostName=host1.com, OAMRestEndPointPort=443, and OAMServerCommunicationMode=HTTPS
